Submenu – Anomaly Shield
This entry page provides direct access to enable, configure, train, and apply Airlock Anomaly Shield protection to applications. Anomaly Shield Applications are configured using resources from the Triggers & Rules and Traffic Matchers tabs.
You can configure multiple Anomaly Shield Applications to analyze requests.
- Each Mapping must be individually configured to specify which Anomaly Shield Application will analyze its traffic. See Assigning mappings to Anomaly Shield applications for more information.
- Multiple Mappings can be configured to the same Anomaly Shield Application.
- A Mapping can only be assigned to one Anomaly Shield Application. It is not possible to assign the same Mapping to multiple Applications.
- To shield an application, machine learning models must be trained. See Part 2 – Training and model enforcement.
Tab – Applications
ON/OFF radio buttons:
- The complete Airlock Anomaly Shield service can be enabled/disabled by the ON/OFF radio buttons. By default, the service is disabled.
In the Applications table, applications that should be protected by Airlock Anomaly Shield can be managed:
Feature | Description |
|---|---|
Anomaly Shield Application | List of configured applications. |
Data Collection | Indicates the state of data collection. Can be enabled (green) or disabled (gray). |
Detection and Response | Indicates the state of detection and response handling. Can be enabled (green) or disabled (gray). |
Enforced Model | Information about the enforced machine learning model. An enforced model is required to enable Detection and Response. Enforced models can be overwritten by enforcing a prepared model in Section – Prepared Model or by importing prepared models. |
Prepared Model | Preparation status and information about the prepared machine learning model. Prepared models can be generated with training data in Section – Training Task. An additional note is displayed on login to the Configuration Center: |
Models | Clicking the button will open the Anomaly Shield model management page page. |
(Delete, add new applications) | List of configured applications. Entries can be added or deleted using the corresponding button. Clicking on an existing entry or adding a new entry to the list will open the Application detail page. |
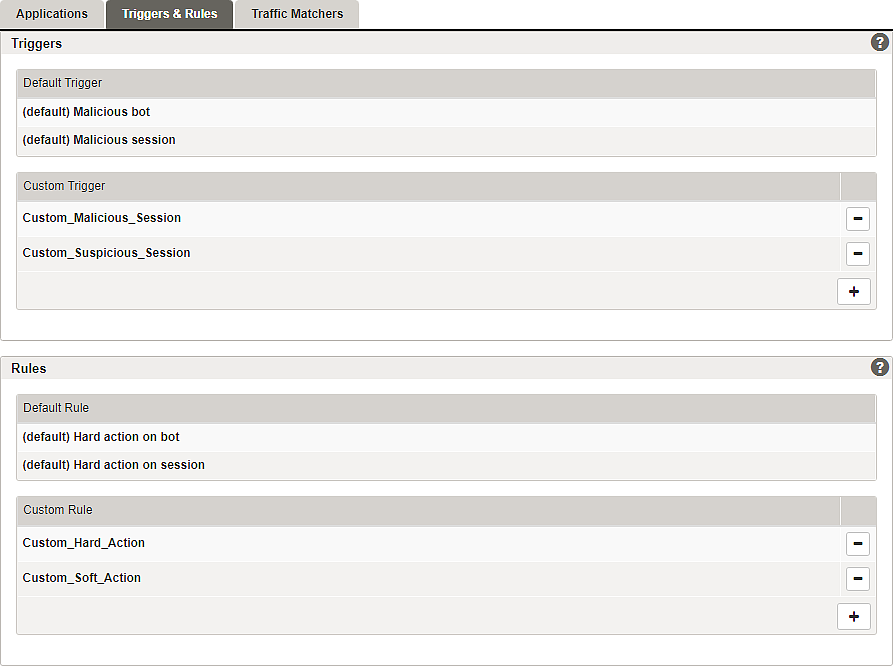
Tab – Triggers & Rules
Airlock Anomaly Shield provides a set of default triggers and rules for general security that cannot be changed. Custom triggers and rules can be added if required and can be selected as resources for individual applications.
Traffic to Anomaly Shield Applications is analyzed, and depending on the Triggers, the configured Rules are enforced.
Rules are processed in top-down order. Sorting can be done by drag and drop, except for default rules. The first matching rule will be applied!
To configure custom Triggers and Rules entries, click on an existing entry or add a new entry to open the corresponding detail pages:
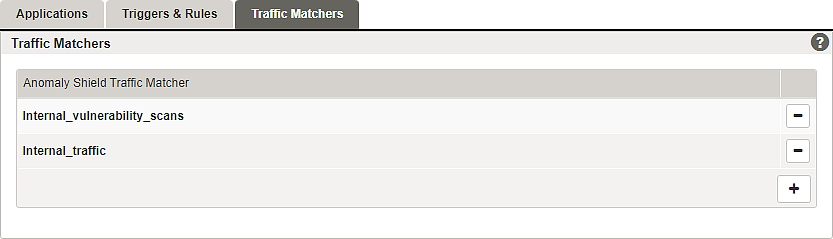
Tab – Traffic Matcher
Traffic Matchers are configured as sets of regex filters and IP Lists that can be applied to incoming traffic.
Traffic Matchers are resources for the Anomaly Shield Applications detail page and can be referenced under:
- Training Data Collection to stop unwanted traffic from polluting training data, e.g., to exclude vulnerability scanning sessions from being collected as training data by Airlock Anomaly Shield.
- Anomaly Detection Exclusions to exclude known traffic from analysis, e.g., internal network monitoring.
- Response Rule Exceptions to bypass Anomaly Shield actions on known traffic. e.g. to allow a vulnerability scan to test an application without disabling the Anomaly Shield on all other traffic.
For configuration, the detail page can be opened by either clicking on an existing entry or by adding a new entry to the list:
Further information and links
Internal links:
- For an introduction including conceptual information, see: Airlock Anomaly Shield
- Configuration is described here: Airlock Anomaly Shield configuration
- For details about anomaly logging, see: Log messages and actions
- For Airlock Anomaly Shield cookies, see: Airlock Anomaly Shield cookies
- Anomaly Shield model management page
- Assigning mappings to Anomaly Shield applications.