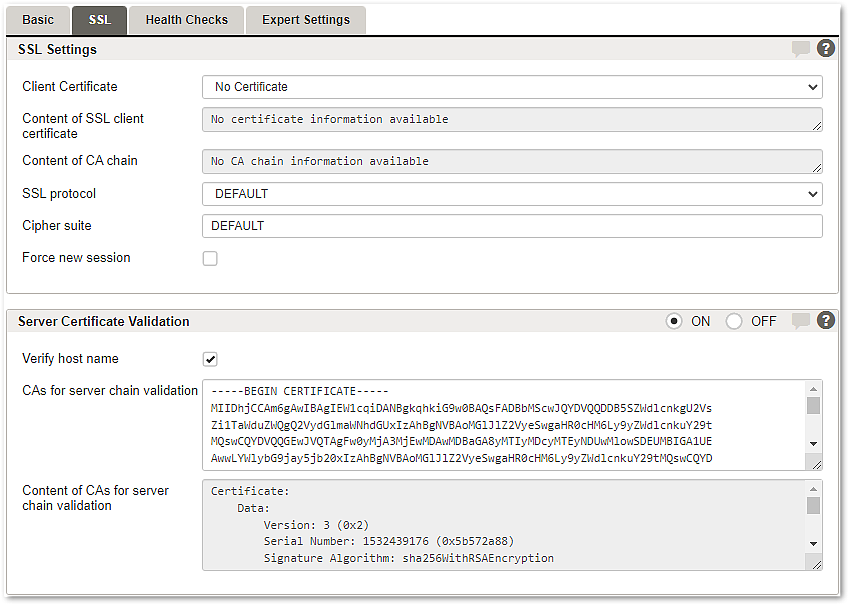
Tab – SSL
Here, SSL settings can be modified to configure the details of the HTTPS connection for a back-end group.
SSL is only applied to back-end hosts that communicate over the HTTPS protocol. Therefore, these settings are validated only if at least one back-end host is configured to use HTTPS.
Section – SSL Settings
Setting | Description |
|---|---|
Client certificate | A selectable list of SSL/TLS certificates for this client. |
Content of SSL client certificate | Shows the content of the certificate. |
Content of CA chain | Shows the certificate chain. |
SSL protocol | The SSL/TLS version which will be used by this back-end can be set here. If the setting is left empty, Airlock Gateway defaults will be used. |
Cipher suite | List the ciphers that the client is permitted to negotiate. If the setting is left empty, the Airlock Gateway default will be used. Restrictions:
|
Force new session | Checkbox to enable/disable forced restart of SSL/TLS handshake. |
We strongly recommend using the default TLS settings of Airlock Gateway in order to mitigate the risk of attacks based on older protocol versions. For example, SSLv3 is not supported by Airlock Gateway 8.0 and higher (configuration activation fails). If you use custom settings, you will also not automatically benefit from optimizations in future Airlock Gateway updates.
Weakening SSL/TLS settings will most likely result in low scores for scanners like ssllabs.com or pentester reporting the security issues associated with old ciphers and protocols.
A list of known attacks on SSL/TLS can be found here: Attacks on TLS and Airlock Gateway Protection Mechanisms.
Section – Server Certificate Validation
Settings to control how back-end server certificates are verified.
Setting | Description |
|---|---|
ON/OFF | Enables or disables the server certificate validation mechanism. Risk When Server Certificate Validation is enabled, you must provide at least one valid CA certificate. Otherwise, the identity of the back-end server cannot be verified. Such an invalid SSL configuration may lead to insecure or failed connections. When Server Certificate Validation is enabled and no or an invalid CA certificate is provided, the following applies:
|
Verify host name | Checkbox to disable/enable hostname verification. Hostname verification requires a server identity check in combination with a valid CA chain to mitigate man-in-the-middle attacks. |
CAs for server chain validation | The certificates of the CA chain to verify the chain of trust. |
Content of CA chain | Shows the certificate chain. |