Configure health checks for Airlock IAM
Airlock Gateway can be configured to check the health status of IAM instances (using the /health/ready endpoint) to prevent requests from the Gateway to an IAM instance that is in a non-healthy state.
By configuring separate IAM instances for the different IAM modules, it is possible to implicitly check the status of individual modules such as Loginapp and Adminapp.
Procedure-related prerequisites
- You must be logged in as an admin in the Airlock Gateway Configuration Center.
- You need CLI access to Airlock IAM to change application parameters and properties.
- You need to restart Airlock IAM to make the changes take effect.
IAM preparation
- In the IAM config file:
Configureinstance.propertiesto allow Gateway access to the IAM endpoint. - Info
You can use a more specific access filter attribute i.e.
10\.10\.\d+\.\d+to restrict the allowed IP range of health checks to Airlock Gateway IP-range only. - The IAM instance allows health requests from remote hosts.
Subsequently, consider configuring dedicated IAM instances per module by sandboxing with profiles or by setting application parameters in the instance.properties file.
Airlock Gateway configuration
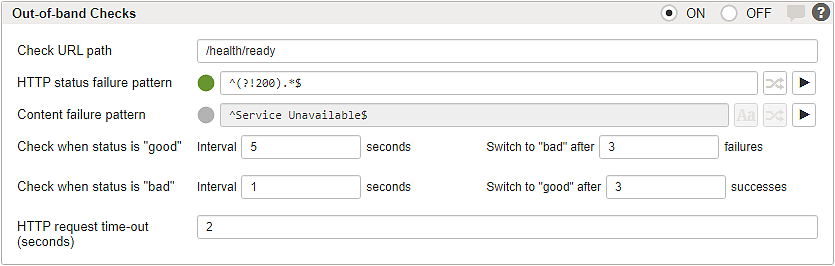
Following this configuration example, the Airlock Gateway checks for non-healthy IAM states.
- In the section Out-of-band Checks in the Back-end Group detail page of the Gateway:
Set the URL path for the IAM health check to/health/ready. - Airlock Gateway does not forward requests to the IAM instance when the health check does not return 200 OK. Note that this is the case when any of the instances modules is in a non-healthy state.