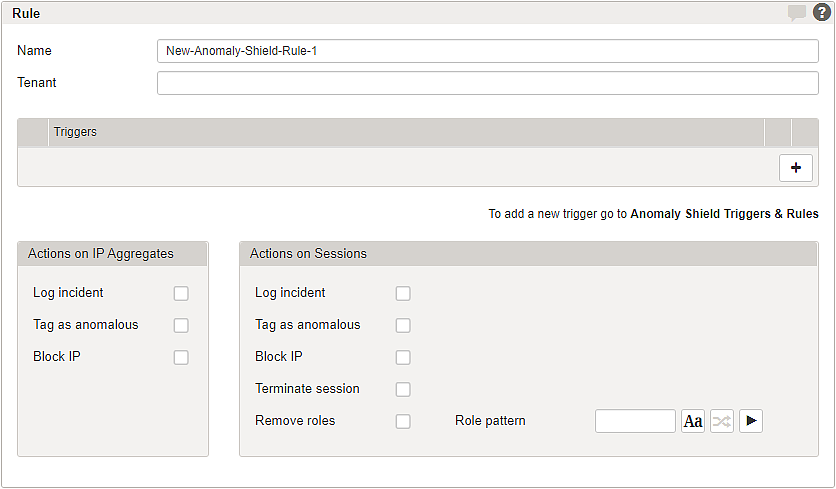
Rule detail page
Rules are used to apply an action in case an Anomaly Shield Trigger has been triggered by potentially threatening incoming traffic to an Anomaly Shield Application. A Rule is a resource for Anomaly Shield Applications and can be referenced under Section – Anomaly Detection in the Response Rules table.
The basic rule parameters are:
Field name/setting name | Description |
|---|---|
Name | Assign a unique name for the rule. |
Tenant | Add tenants to allow tenancy access. See also Multitenancy feature |
Triggers | Select one or more triggers to be applied by this rule. |
Actions on Sessions
The options in this section allow configuring how to handle regular sessions when one or more trigger patterns have been triggered.
Field name/setting name | Description |
|---|---|
Log incident | Enable/disable incident logging. |
Tag session as anomalous | Enable/disable anomalous tagging in logged incidents using |
Terminate session | Enable/disable session termination. |
Block IP | Enable/disable IP blocking. The default blocking time is set to |
Remove roles with Role pattern | Regex filtering to withdraw roles in case the anomaly rule has been triggered. Removing the role-based access can trigger a re-authentication, e.g., requesting a 2FA token. Note that role removal is executed only once per session. |
Actions on IP Aggregates
The options in this section allow configuring actions for virtual sessions based on IP aggregates. Airlock Anomaly Shield detects and aggregates sessions from the same client IP address into one virtual session if any option is enabled.
This allows for identifying suspicious IP addresses (e.g., from a bot node or automated tools) and detecting fragmented attacks that may span multiple regular sessions. Suspicious IPs can then be temporarily blocked.
Field name/setting name | Description |
|---|---|
Log incident | Enable/disable incident logging. |
Tag as anomalous | Enable/disable anomalous tagging in logged incidents using |
Block IP | Enable/disable IP blocking. The default blocking time is set to |
Note that IP aggregates will not prevent an attacker from continuing attacks blocked by session actions, if the Block IP action is not enabled for IP aggregates.
Further information and links
Internal links:
- For trigger configuration, see Trigger and Pattern detail page.
- Tab – Triggers & Rules as the entry point to this detail page.
External links:
- (IAM documentation) Risk-based authentication