Use case: FIDO passkeys as first auth factor in IAM
This article explains how to use FIDO passkeys as a first authentication factor. This can be both in parallel with password authentication or as a standalone authentication factor.
Goal
- Learn how to use FIDO passkeys as a primary authentication factor in Airlock IAM.
- Get to know different usage types.
Initial thoughts
End-user authentication with FIDO passkeys can be done in several ways. One of them is using passkeys as a first authentication factor, typically as an alternative to or as a replacement for the password.
Airlock IAM has several FIDO steps supporting different usage scenarios, which are described in the following sections.
All usage scenarios have the following in common:
- IAM acts as the FIDO relying party.
- The FIDO steps can be combined with a second factor or used as the only authentication factor.
- In all cases, goto buttons can be used to offer alternative authentication factors to the end-user. For more details, see Goto (flow concept).
Usage 1 - Username followed by FIDO
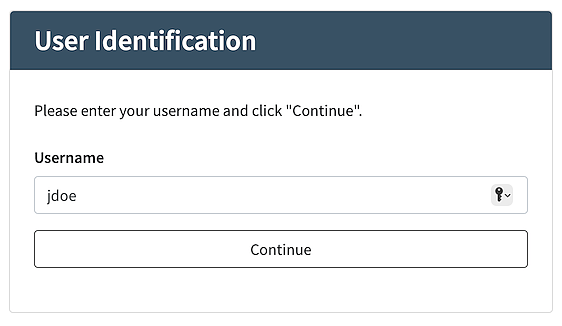
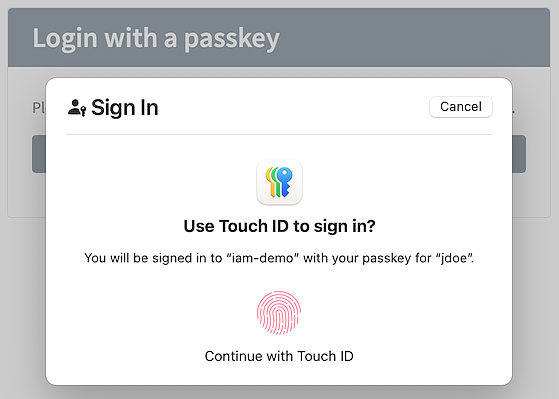
In this scenario, the user first enters their username. If the username is valid, the user uses the FIDO passkey to log in.
- Image:
- User Identification Step
- Image:
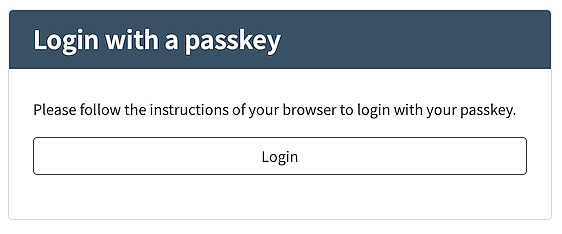
- Information step
- Image:
- FIDO Authentication Step
Properties
- Works with all types of FIDO authenticators.
- Can be combined with other authentication types (e.g., fallback to a password or another factor).
- Includes multiple pages and clicks, but provides strong end-user guidance (with the information page).
Configuration hint:
- Use the User Identification Step plugin as the first step.
- Use the FIDO Authentication Step plugin as the second step.
This scenario is similar to using FIDO as a second factor. The only difference is that here, the process starts with the User Identification Step. For further information about FIDO as a 2nd factor, see Use case: FIDO passkey as 2nd factor or approval step in IAM.
Usage 2 - Username with FIDO autofill
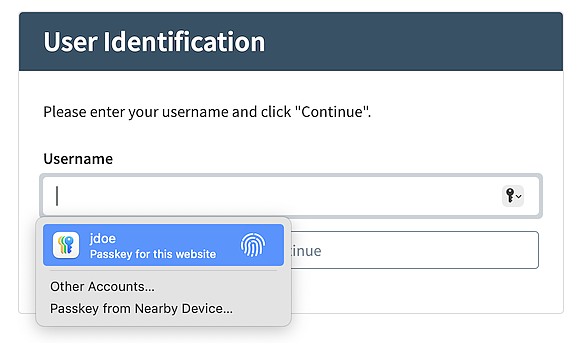
This usage scenario is similar to the first one, except it already tries to discover available FIDO keys when the login page with the username input field appears. The discovered keys are suggested to the user, allowing for a quick and simple login process.
The exact user experience depends on the web browser. Ideally, the user uses the biometric sensor to unlock the FIDO authenticator to log in - without having to type anything.
- Image:
- Username Identification Step with FIDO autofill.
Properties:
- Optimal user experience - ideally no typing required.
- Best suited when some or all end-users do not have a password.
- Can be combined with other authentication types (e.g., fallback to a password or another factor).
- Works with discoverable FIDO keys.
Configuration hint:
- Use the User Identification with FIDO Authentication Step plugin.
- Note the two Tags On Success properties in the plugin: They are important to use the step securely.
- Use a fallback authentication step (e.g., the Password-only Authentication Step) just after this FIDO step. Use the skip condition such that the fallback authentication step is only used if authentication with FIDO fails.
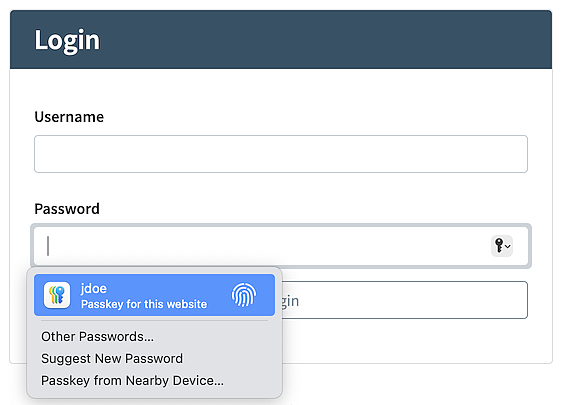
Usage 3 - Username and password with FIDO autofill
This usage scenario is similar to the second one, but it also includes a password input field.
- Image:
- Username Password Authentication Step with FIDO autofill.
Properties:
- Provides an optimal user experience if username-password authentication is a desired fallback mechanism.
- Ideal if some or all users still have a username and a password.
- Works with discoverable FIDO keys.
Configuration hint:
- Use the Username Password with FIDO Authentication Step plugin.
- Note the two Tags On Success properties in the plugin: They are used to distinguish whether the user has logged in with username and password or with FIDO.