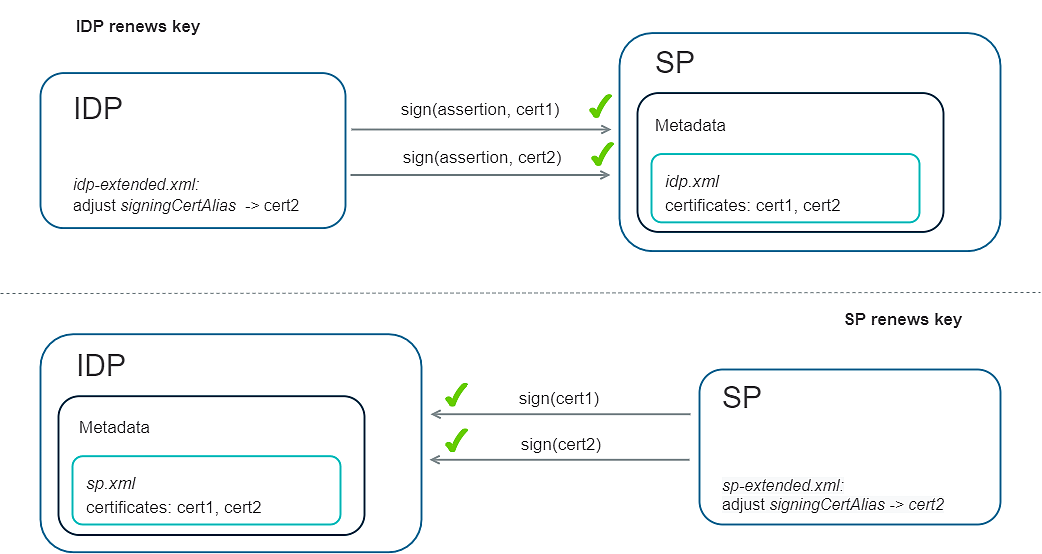
Asynchronous renewal of the public key in the signing certificate
In SAML, communication between the Identity Provider (IDP) and Service Providers (SPs) is cryptographically secured. Each IDP and SP stores its signing key pair in its key store, while the public keys (wrapped in X.509 certificates) are included in the metadata files idp.xml and sp.xml.
Both the IDP and the SPs must sometimes renew their public keys. This may be the case if the key gets compromised or if it will be replaced by a longer, more secure key. IAM supports multiple signing certificates in a single metadata file, allowing old and new keys to coexist. This makes it possible to rotate the signing keys asynchronously, without requiring all parties to switch at the same time.
This article explains how to renew the public key in the signing certificate asynchronously. It first covers renewal by the IDP, then by the SP. In both cases, IAM may act either as IDP or SP.
This article is about renewing the public key. In the context of this article, expiration of the certificate itself is irrelevant. The certificate only serves as a wrapping of the public key.
Also, the described procedure only works for key renewal in a signing certificate.
The IDP renews the public key in the signing certificate
The next table shows the steps required from both the IDP and SPs when the IDP renews the public key in the signing certificate.
Step | Performed by the IDP | Performed by the SP |
|---|---|---|
1 | The IDP creates a new signing key pair and stores it in its key store. | |
2 | The IDP adds the new public signing key in the form of an X.509 certificate to the | |
3 | The IDP shares the new signing certificate with the respective SPs. There are two options:
| |
4 | Each SP either adds the new signing certificate to the existing
| |
5 | The IDP informs the SPs in time about the IDP's certificate renewal date. | |
The SPs do not have to switch at the same time, as the old and new certificate can coexist in the updated | ||
6 | On rollover date, the IDP adjusts the
| |
7 | After rollover, the IDP should
If IAM acts as IDP, this change requires a restart of the IAM instance. | |
After rollover, each SP should
If IAM acts as SP, this change requires a restart of the IAM instance. |
The SP renews the public key in the signing certificate
The next table shows the steps required from IDP and SP when an SP renews the public key in the signing certificate.
Step | Performed by the IDP | Performed by the SP |
|---|---|---|
1 | The SP creates a new signing key pair and stores it in its key store. | |
2 | The SP adds the new public signing key in the form of an X.509 certificate to the | |
3 | The SP shares the new signing certificate with the respective IDP. There are two options:
| |
4 | The IDP either adds the new signing certificate to the existing
| |
5 | The SP informs the IDP in time about the SP's certificate renewal date. | |
The IDP does not have to switch at the same time, as the old and new certificate can coexist in the updated | ||
6 | On rollover date, the SP adjusts the
| |
7 | After rollover, the SP should
If IAM acts as SP, this change requires a restart of the IAM instance. | |
After rollover, the IDP should
If IAM acts as IDP, this change requires a restart of the IAM instance. |