SAML Single Logout (SLO)
Besides techniques for Single Sign-On, SAML also defines two techniques for Single Logout (SLO) that are supported by Airlock IAM:
IDP-initiated SLO
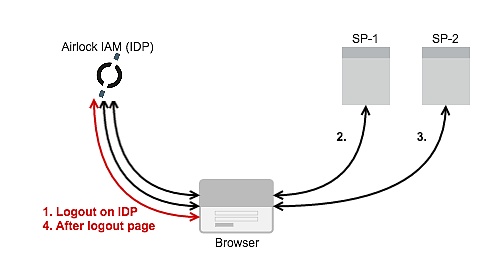
With IDP-Initiated SLO the initial logout process is started on the Airlock IAM-IDP:
- A logout is started on the Airlock IAM IDP.
- The browser is redirected to the first SP for logout and is always redirected back to the IDP, no matter if the session with SP-1 was still active.
- The browser is redirected to the second SP for logout and is always redirected back to the IDP, no matter if the session with SP-2 was still active.
(at this point further logouts on further SPs could be performed, but they were omitted in the figure for simplicity, however, logouts are only performed to SPs the user previously got an Assertion for).
- When after the last logout the browser returns to the Airlock IAM-IDP the after-logout-page is returned by the Airlock IAM-IDP.
SP-initiated SLO
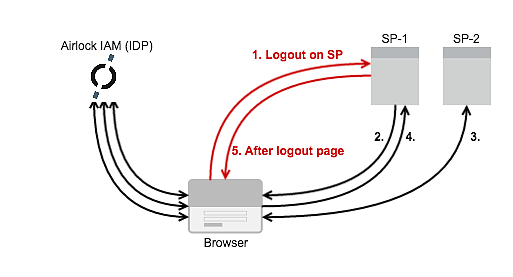
- A Single-Logout is initiated on one of the SPs (here SP-1).
- The SP sends a “Logout Request” via the browser to the Airlock IAM-IDP.
- The Airlock IAM-IDP performs the logout on SP-2 (and any further SPs which always redirect back to the IDP).
- Now the user is logged out locally on the IDP and the browser is redirected back to the initiating SP-1 with a final “Logout Response” confirming that the Single-Logout is completed.
- The after-logout-page is sent to the browser by the SP-1
SLO and SESSION=CLEAR
The configuration of the Gateway's SLO behavior depends on the setup's architecture. If the same gateway protects SPs and the IdP, then the client has one single session to the gateway to connect to all actors. During SLO, the termination of this client session must be managed carefully to avoid a situation where the client is no longer able to connect to the SP.
There are two setting options:
- If the Clear Gateway Session on Single-Logout property is enabled, the gateway will immediately clear all credentials and sessions as soon as SLO starts. This is the safest option, because it ensures that no credentials or sessions can be misused, even if the logout process is not completed for all SPs.
- This setting is recommended for setups where no SPs are behind the gateway managing the client session.
- This setting is recommended in situations where no additional post logout actions are executed on the terminated session after the SPs have completed.
- If the Clear Gateway Session on Single-Logout property is disabled, the gateway will wait to delete credentials and sessions until the SLO process is fully finished. This configuration will work correctly in any setup involving the gateway and SPs. However, there is a small risk that credentials and sessions will not be cleared if the SLO process does not finish properly.
It may be necessary to configure a Temporary Single-Logout Gateway Credential. This credential is required by the Gateway to access the SPs, if the SP's SLO endpoint enforces access restrictions.
Further information and links
- See SAML Single Logout with temporary Gateway role for more information about SLO configuration.