Privilege escalation protection
Privilege escalation protected administrator roles (PEPAR) in the Adminapp protect certain administrative functions against privilege escalation.
The concept is applicable to all Adminapp roles but focuses on the following features:
Feature | PEPAR benefit |
|---|---|
Administrators management | Creating new Adminapp users or assigning roles to existing administrators may lead to privilege escalation. PEPAR - if configured accordingly - prevents it. Group of actions in the Role-based Access Control plugin: Administrator management |
Configuration | Adminapp users with the right to edit and activate the IAM configuration may grant themselves all possible privileges by editing the configuration. Roles including these rights are therefore susceptible to privilege escalation. PEPAR - if configured accordingly - prevents it. Group of actions in the Role-based Access Control plugin: Configuration management |
PEPAR roles
To define what subset of Adminapp roles is to be protected by PEPAR, the IAM configuration allows to explicitly list these roles.
To do so, go to: Adminapp >> Administrators >> Administrators Management >> Privilege Escalation Protected Admin Roles (PEPAR)
The listed roles are called PEPAR roles in the following.
PEPAR authorization rules
The following rules apply for PEPAR protected roles:
- Administrators with PEPAR roles can only be managed (list, view, edit, delete) by administrators with PEPAR roles.
- PEPAR roles can only be assigned to or unassigned from administrators by administrators with PEPAR roles.
In other words, administrators without PEPAR roles can neither manage administrators with PEPAR roles nor assign PEPAR roles.
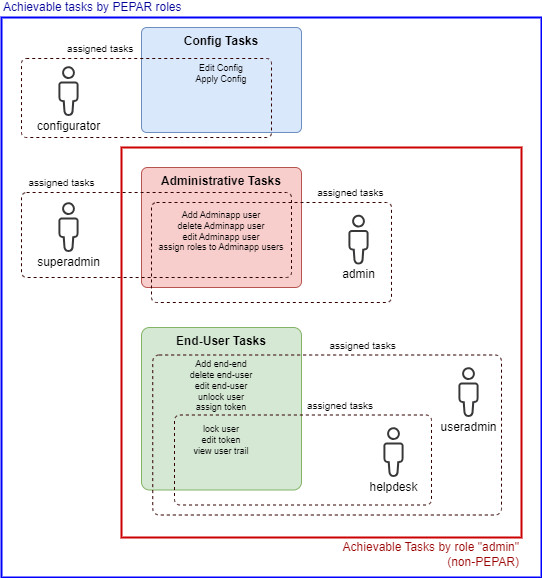
Example use case
This example is used to illustrate the PEPAR feature. It assumes the following Adminapp roles:
Role | Privileges (actions) | Description |
|---|---|---|
| Manage Adminapp users | A super administrator that can create and edit all other Adminapp users and assign roles. Role needs PEPAR protection! |
| Edit and apply IAM configuration | For users allowed to edit the IAM configuration and apply the changes to the system. Note that Adminapp users with this role may also re-configure Adminapp access control. Role needs PEPAR protection! |
| Manage Adminapp users | Adminapp users with this role are allowed to create, manage, and delete Adminapp users with non-PEPAR roles. |
| Create and edit end-users. Assign and edit authentication tokens. | For Adminapp users that are allowed to create, edit and delete end-user accounts, assign roles to end-users and manage the end-users' authentication tokens. |
| View end-users and other actions on end-users. | Helpdesk users with the minimum required actions on the end-user accounts to do their job. |
Note that all Adminapp users with the superadmin and/or the configurator role can gain all possible privileges, while Adminapp users with other roles (including the admin role) are strictly limited in terms of privileges.
The following diagram visualizes the situation:
Configuration
Prerequisite: All PEPAR roles must also be present in the Assignable Role Combinations plugin configuration.
- Go to:
Adminapp >> Administrators >> Administrators Management - In the section Privilege Escalation Protected Admin Roles (PEPAR) add one or more PEPAR roles.
Migration
For existing setups, no migration is required. Without the configuration of the PEPAR protected roles, the authorization system for administrators continues to work unchanged and may remain vulnerable to privilege escalation.
Limitations
PEPAR is limited to protect against privilege escalation within the Adminapp. It does not protect against users with access to:
Configuration | With access to the configuration, a user may change the role setup and the PEPAR configuration and therefore escalate privileges. |
Database | With access to the database, a user may modify the administrator to role assignments and therefore escalate privileges. |
Further information and links (optional block)
- Segregation of duties provides more information on the creation of administrator roles.
- See Privilege escalation prevention for PEPAR Security Best Practices.