Submenu – Geolocation Filter
The geolocation filter allows blocking traffic based on origin countries. Requests are blocked early at the network firewall in order to save system resources in case of a DoS (Denial of Service) attack. Hence, blocks caused by the geolocation filter are not visible in any log file.
For redirecting requests based on geolocation information, please use the corresponding request action.
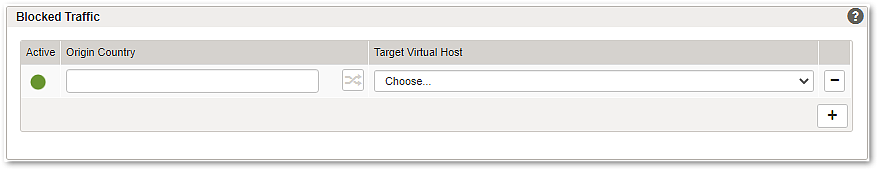
Section - Blocked Traffic
Geolocation filter rules have the following configuration attributes:
Active
Rules may be set active or inactive. This allows for preparing and quickly enabling rules in case of an emergency. As an example, if most users access applications from a specific geographic region it may be useful to prepare a geolocation rule that blocks access from any other region. In case of a DoS attack, the rule may be enforced quickly to block all requests from outside the main user base and protect Airlock Gateway resources.
Origin Country
For each rule, a list of origin countries can be specified. The country codes correspond to the Alpha-2 codes in the ISO 3166-1 standard. If more than one country code is specified, the rule applies if any of the countries is matched (OR combination). The country condition can be inverted. For example, to block all traffic from outside the DACH region, specify countries “DE, CH, AT, LI” and invert the condition.
Target Virtual Host
Geolocation rules may be restricted to traffic targeting certain virtual hosts. This allows differentiating between applications with diverse user bases. Options are to select an individual virtual host or “any”, in case the rule applies to all incoming traffic.
Geolocation rules are based on IP addresses. That is, if a target virtual host is selected, the rule applies to all virtual hosts sharing the same IP addresses as well.
Further information and links
- For geolocation cookies, see: Geolocation cookies