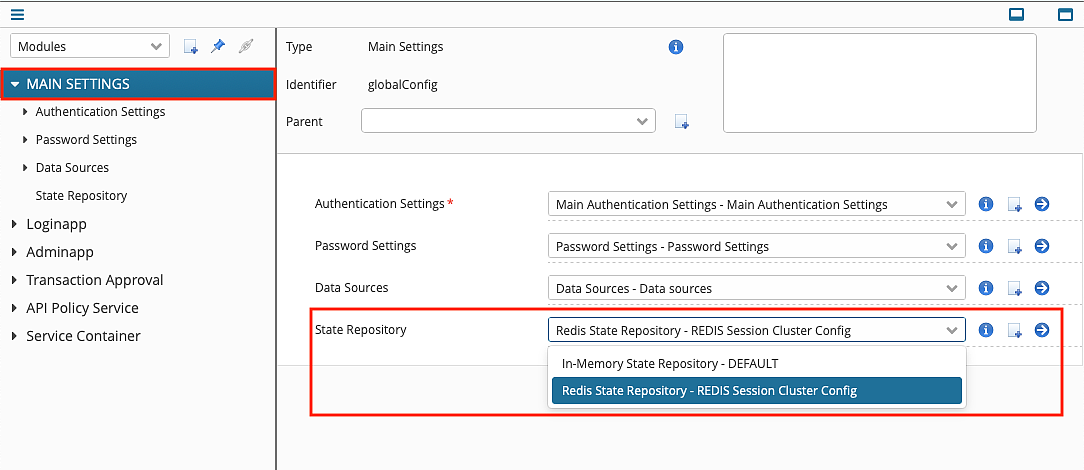
This article describes how to store Airlock IAM session state in a Redis session repository.
Airlock IAM relies on session state stored server-side. Most requests processed by Airlock IAM must be able to access the up-to-date session state. If multiple IAM instances are active, how session information is stored and that it can be shared among the IAM instances is relevant.
As of IAM 8.2, the feature is available for the Loginapp, Adminapp, and Transaction Approval modules.
What is Redis?
Redis is a fast and proven open-source data storage solution that can be used as a distributed cache.
- There are two places to store session state:
- In the local memory of the IAM instance. This is the default.
- In an external Redis session repository. How to set this up is described in this article.