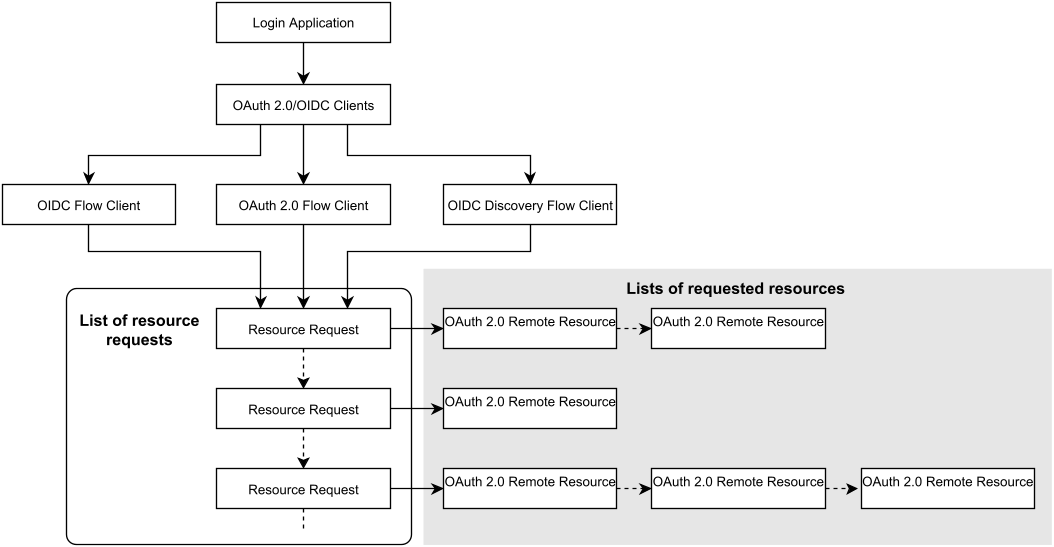
IAM can process user claims - pieces of information about a user - from different resources and use them in authentication flows and identity propagation.
In this context, the term resource refers to sources of claims and should not be confused with the Resource Server defined in OIDC. In the IAM configuration, use resource mappings to map remote resources to the local IAM user.
- Possible sources of claims are:
- ID token
- Remote service endpoints (e.g.,
userinfoendpoint)
- Possible types of claims are:
- User identities (
username,sub,issuer,aud, etc.) - Roles
- Context data
- Information related to authentication and authorization (ACR values, scopes, etc.)
- Technical information (validity, etc)
To determine the user identity of the foreign authorization server, it is required to configure at least one resource mapping that defines the username.
- In addition to the username, any other resources available may be mapped at login:
- User role resources will map their values into the authentee roles of the user logging in.
- User context data resources will map their values into the authentee context data.
In order to avoid ambiguity and to ensure a valid username, exactly one Remote Username Resource must be configured.
In OpenID Connect, it is possible to use an ID Token resource (claim) instead of requesting a remote resource to be mapped.