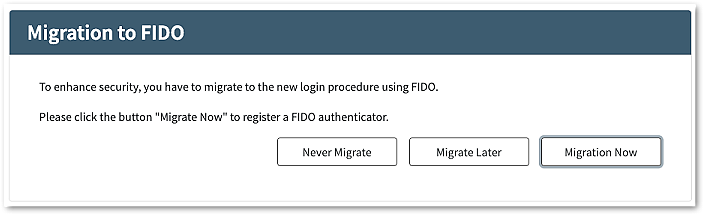
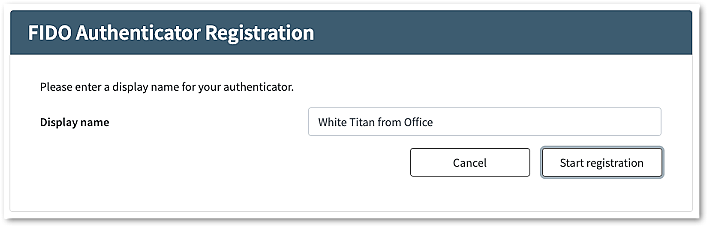
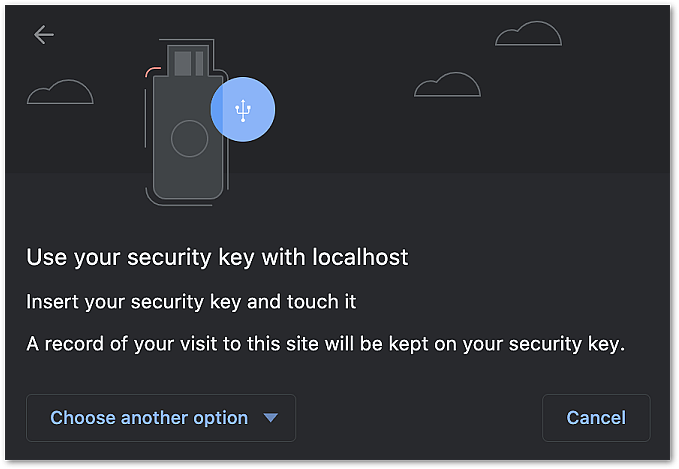
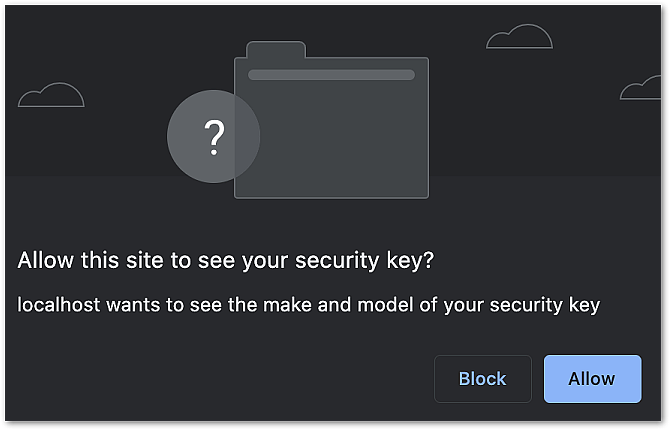
This article describes the token migration self-service that can be used to move end-users from using an arbitrary second factor to using FIDO.
The described process allows end-users to register a FIDO authenticator during the login process.
To register FIDO authenticators after the login process, i.e. for already authenticated end-users, see Use case: FIDO registration self-service instead.
Note that FIDO credentials can be managed by administrators in the IAM Adminapp, but they can only be registered by the end-user in a self-service.