The Remote Consent Protocol is embedded in the OAuth 2.0 Authorization Code Grant Flow and begins after the end-user has been authenticated itself in IAM.
The following parties are involved:
Party | OAuth 2 Concept | Authorization Code Flow | Remote Consent Protocol |
|---|---|---|---|
End-User (Browser) | User-Agent | ||
Third-Party Application | Client | ||
Airlock IAM | Authorization Server (AS) | ||
Remote Consent Application | - |
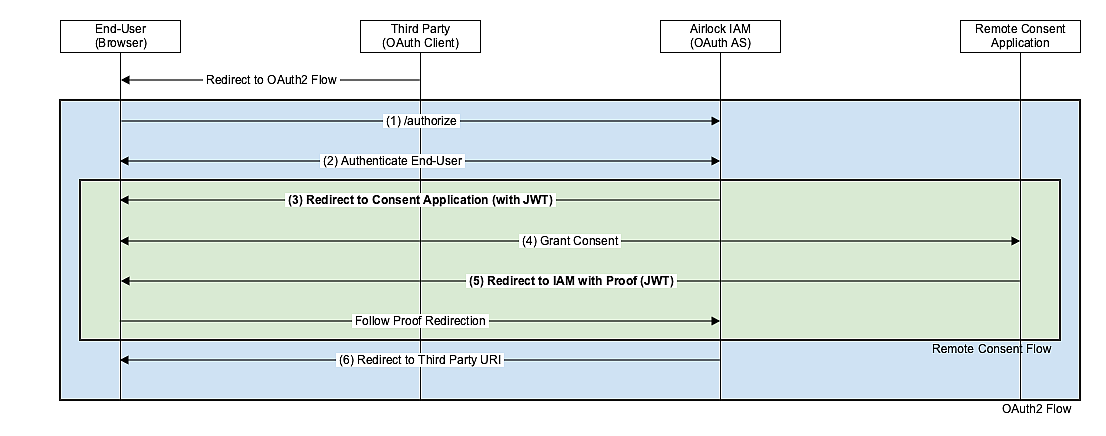
The Remote Consent Flow (green) is embedded in the OAuth 2.0 Authorization Code Flow (blue) such that it can be executed instead of displaying the IAM's consent page.
The Remote Consent Protocol (green) is as follows:
Step | Description | Details |
|---|---|---|
(1)/(2) | Standard authentication steps. | – |
(3) | After the end-user has been authenticated: IAM redirects the end-user's browser to the Remote Consent Application. | With the redirect, IAM sends several HTTP GET parameters. Example Redirect URL (not URL-encoded): /ebanking/display-consent?lang=de&consent_token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVC... (JWT truncated)
|
(4) | The end-user interacts with the Remote Consent Application to give the consent: The Remote Consent Application reads and verifies the JWT "consent_token" to display the consent screen to the end-user. | – |
(5) | The Remote Consent Application redirects the end-user's browser back to the callback_uri and puts an encrypted and signed JWT as GET parameter |
Example Redirect URL (not URL-encoded): /auth/oauth2/v3/confirm-consent?consent_token=eyJhbGciOiJIUzI1NiIsInR5c... (JWT truncated) |
(6) | Airlock IAM verifies the JWT from the Remote Consent Application |
|





