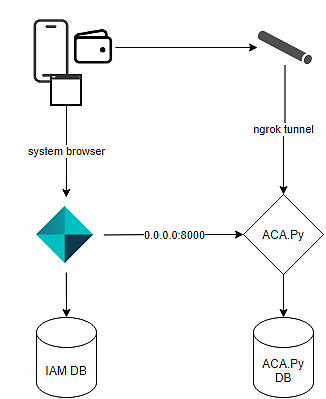
Self-Sovereign Identities (SSI) is the underlying standard for the new E-ID in Switzerland and the EUDI in the European Union. The standard is still evolving, and many questions regarding the protocols and formats will only be answered in the next couple of months or even years.
Nevertheless, the concept of Self-Sovereign Identities is a game changer in how citizens, customers, and employees share data with authorities and companies. To allow customers to explore these new opportunities, we have implemented a functionally rich yet still simple solution for Self-Sovereign Identities in Airlock IAM.
Self-Sovereign Identities is an incubating feature. It is intended to implement proof-of-concept use cases and it is expected that the plugins provided will change fundamentally and without further notice in future releases of Airlock IAM.