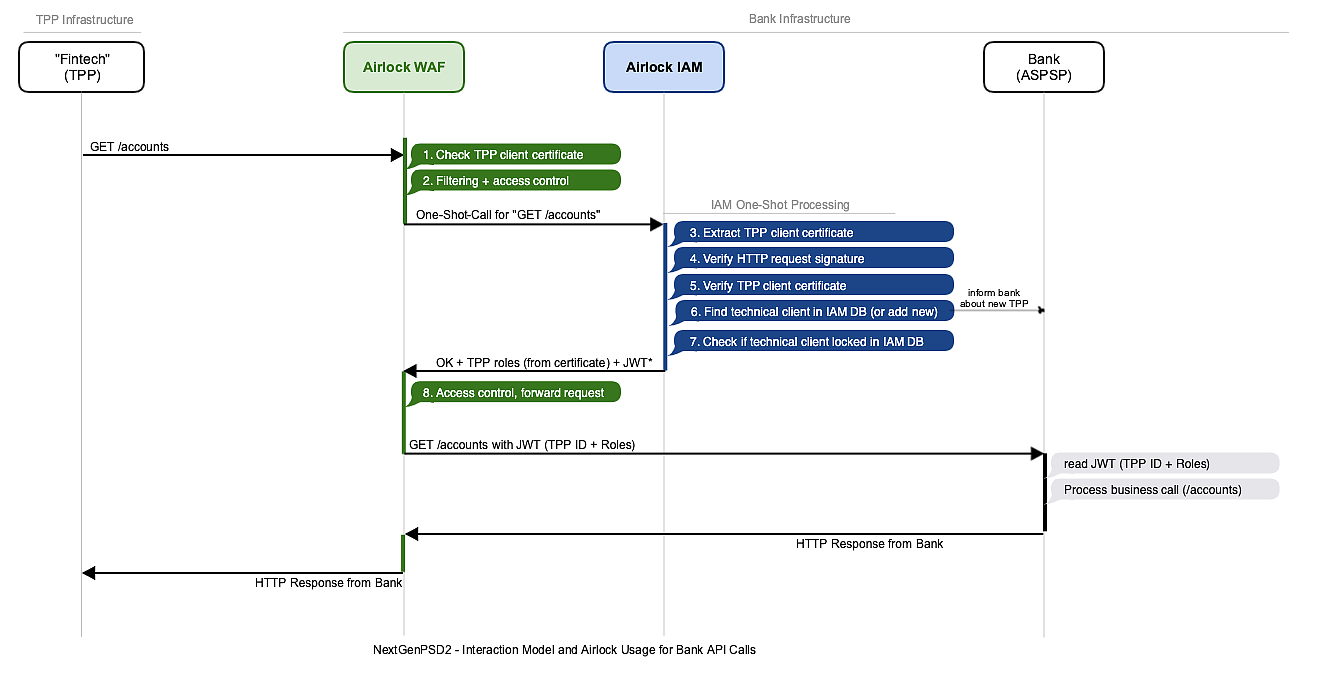
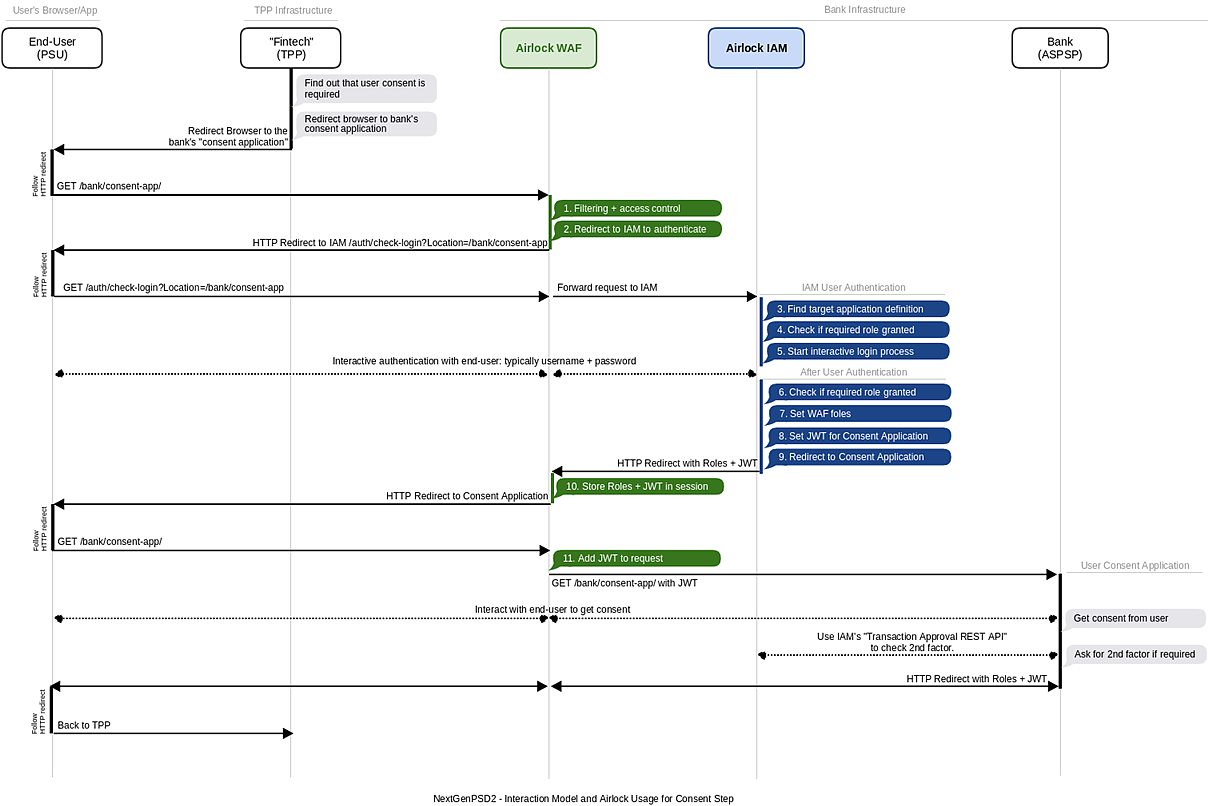
| Filtering and access control | | Filter request as usual (allow rules, deny rules, etc.) and check if session is authorized. In the flow diagram, we assumed that the session is not authorized. If the user has already authenticated before and the session already contains the necessary role, directly continue with step 11. |
| Redirect to IAM to authenticate | | Since the required role is missing in the Gateway's session, the end-users browser is redirected to IAM's "check-login" end-point. |
| Find target application definition | | Based on the forward location ("Location parameter" = the URL the end-user initially tried to access), IAM finds the corresponding target application definition. It holds information about required roles and identity propagation. |
| Check if required role granted | | Checks whether the end-user has already authenticated and whether the session is already entitled to access the bank's consent application. |
| Interactive Login Process | | If required, IAM authenticates the end-user interactively. This is typically done by responding with "login page" to check username and password but is generally open for any other type of authentication. Note that the 2nd authentication factor (SCA) is typically not part of this authentication process: it will be triggered by the bank's consent application in a later step only if necessary. |
| Check if required role granted | | Check if the required role has been granted after successful authentication. If not, abort. |
| Set Airlock Gateway roles | | Inform the Gateway about the granted roles, so the Gateway can let the original request (1) pass later on. |
| Set JWT for Consent Application | | Store a JWT with the end-user's name, roles (and optionally other information) in the Gateway's session store. The JWT will later be sent to the bank's consent application. |
| Redirect to Consent Application | | Redirect the browser to the bank's consent application. |
| Store Roles and JWT in session | | Stores the roles and JWT in the session store, i.e. this information is not sent to the end-user's browser. |
| | | Add JWT with username and roles to the request for the bank's consent application. |