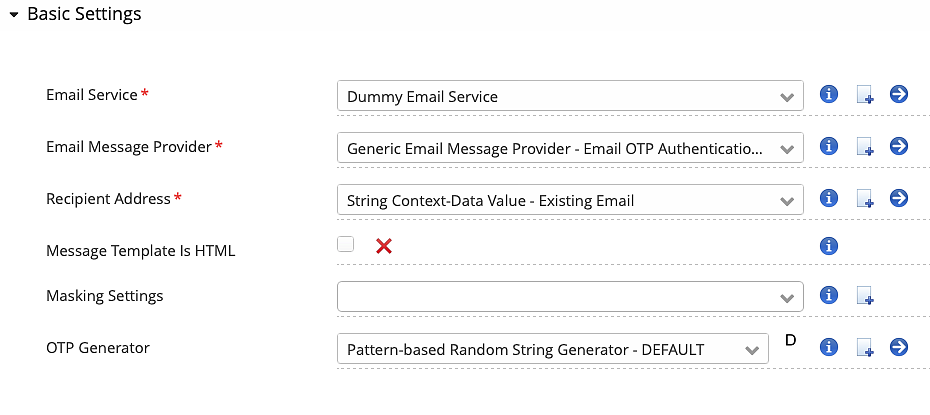
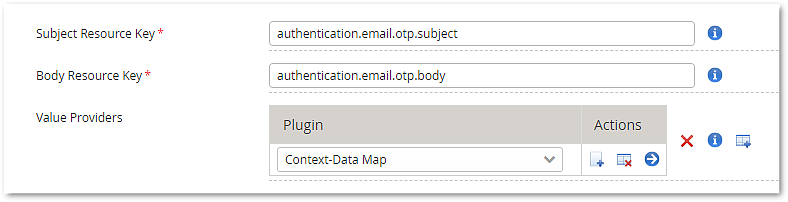
This use case describes the configuration of the Email OTP Authentication Step. It assumes that there is a valid target application configuration with a Username Password Authentication Step.
The following configuration example features the new Email OTP Authentication Step that has been implemented with Airlock IAM 7.7. The new implementation allows multi-lingual subject and body texts with variables.
The old email OTP authentication step has been renamed to Legacy Email OTP Authentication Step and is still available.