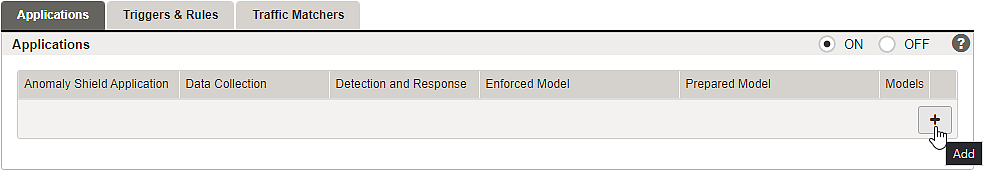
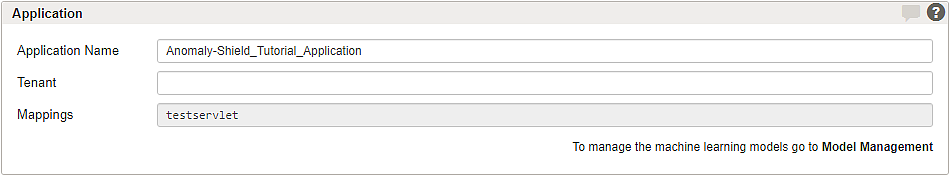
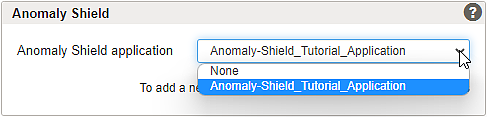
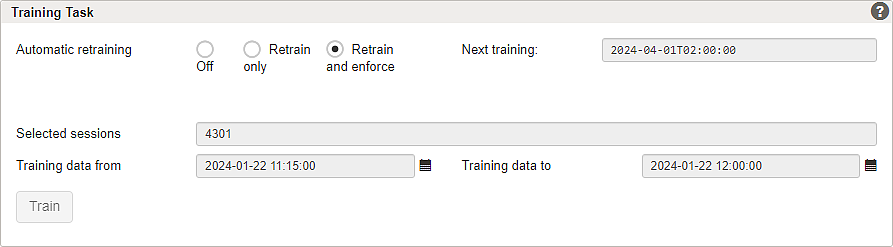
One or more Anomaly Shield applications must be configured to shield back-end groups and applications with Airlock Anomaly Shield. Subsequently, Airlock Anomaly Shield's machine learning algorithms must be trained with production data to detect anomalous or suspicious traffic effectively.
In general, different back-end applications and similar back-end applications serving different business cases have different traffic behaviors. In this case, individual Anomaly Shield applications should be configured for each mapping and not be shared by different mappings.
- Best practice regarding initial Anomaly Shield application setups is to start by configuring individual Anomaly Shield applications per mapping and observing the traffic:
- When several thousand sessions occur weekly, stick with the multi Anomaly Shield application setup (one application per mapping).
- When only a few hundred sessions occur per day/week, consider sharing one Anomaly Shield application for similar back-end applications so that a sufficient amount of similar traffic is cumulated.
See also the supplementary article Recommendations for assigning mappings to Anomaly Shield applications.