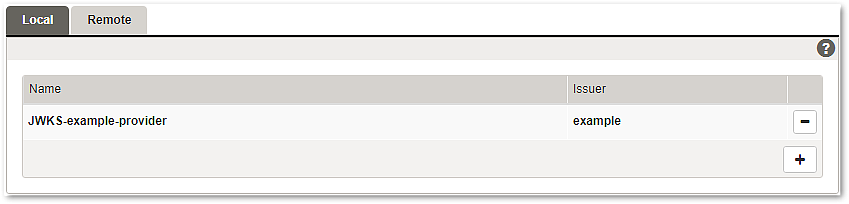
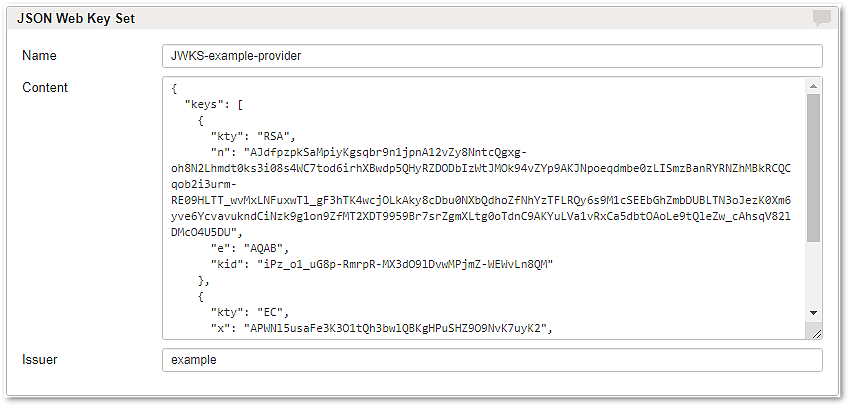
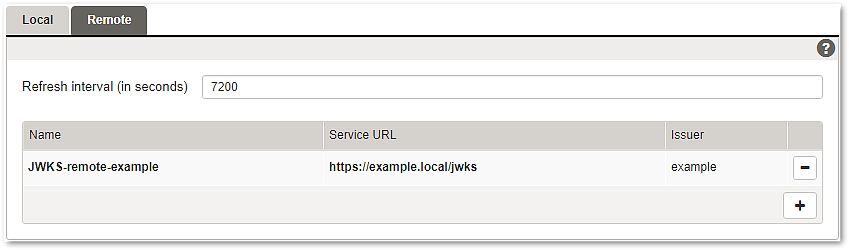
JWK is a JSON representation of cryptographic keys widely used in the context of JWT. A set of such keys is known as JWKS, a JSON Web Key Set. JWKS is also the format used by the gateway to configure verification of access tokens.
When a JSON Web Key Set provider is configured to be used in a mapping, the keys in the set will be consulted when trying to verify a JWS or when decrypting a JWE.
- The gateway uses a 2-stage filtering process to reduce the number of processed keys:
- Stage 1 – JWKS are filtered by their Issuer information.
- Stage 2 – The individual keys of the selected JWKS are finally filtered according to their key properties.