Airlock Gateway supports automatic CSRF token injection and validation to protect sessions against CSRF (Cross-Site Request Forgery) attacks.
- If CSRF tokens are enabled, Airlock Gateway adds a random CSRF token to responses delivered by back-ends before they are sent to the client.
- Subsequent requests (form posts or AJAX requests) must include the CSRF token to be accepted except for the request types GET, HEAD, and OPTIONS.
If session-based URL encryption is enabled, sessions are already protected against CSRF except for URLs that have been configured as path exceptions. A common reason for URL path exceptions is URLs that are dynamically generated on the client.
However, for URLs that are not URL encrypted, we recommend enabling CSRF tokens as a complementary measure for CSRF protection.
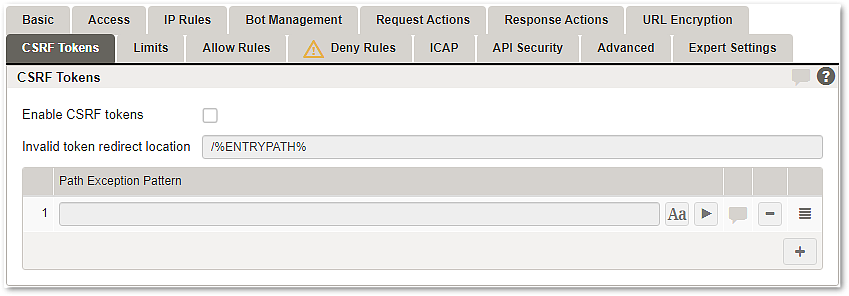
Enable CSRF tokens | Enables automatic CSRF token injection and validation on this mapping. |
Invalid token redirect location | If a missing or invalid CSRF token is detected, the client is redirected to the configured location (e.g. to The token redirect location must be configured as a path exception if it is located behind the same URL mapping. Otherwise, a continuous redirect loop is initiated. Invalid tokens may occur because of session timeouts or terminated sessions and do not necessarily imply active attacks. |
Path Exception Pattern | All incoming URLs that match one of these patterns are accepted by Airlock Gateway without a valid CSRF token. The ignore case (ICase) option specifies whether the pattern is matched case-sensitively or not. Exception patterns are configured in a list of regular expressions. The following example adds the URL Example: To allow requests without CSRF tokens to the root directory of the mapping use the following configuration example: Example: |