SSL settings can be modified here to configure the details of the HTTPS connection for an individual virtual host.
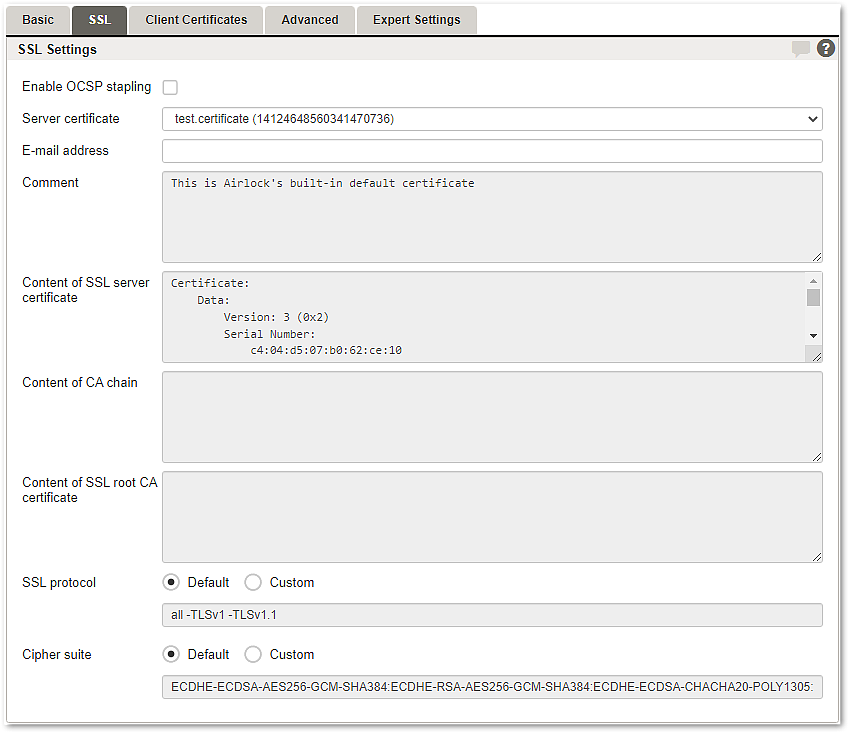
Enable OCSP stapling | This option enables Online Certificate Status Protocol OCSP stapling. The Online Certificate Status Protocol (OCSP) was created as an alternative to the Certificate Revocation List (CRL) protocol. Both protocols are used to check whether an SSL Certificate has been revoked.
|
Server certificate | The SSL/TLS certificate for this virtual host. |
E-mail address | The email address of the server administrator.
|
Content of SSL server certificate | Shows the content of the certificate. |
Content of CA chain | Shows the chain of trust of the certificate chain.
|
Content of SSL root CA certificate | Shows the content of the certificate. |
SSL protocol |
|
Cipher suite |
|
We strongly recommend using the default TLS settings of Airlock Gateway in order to mitigate the risk of attacks based on older protocol versions. For example, SSLv3 is not supported by Airlock Gateway 8.0 and higher (configuration activation fails). If you use custom settings, you will also not automatically benefit from optimizations in future Airlock Gateway updates.
Weakening SSL/TLS settings will most likely result in low scores for scanners like ssllabs.com or pentester reporting the security issues associated with old ciphers and protocols.
A list of known attacks on SSL/TLS can be found here: Attacks on TLS and Airlock Gateway Protection Mechanisms.