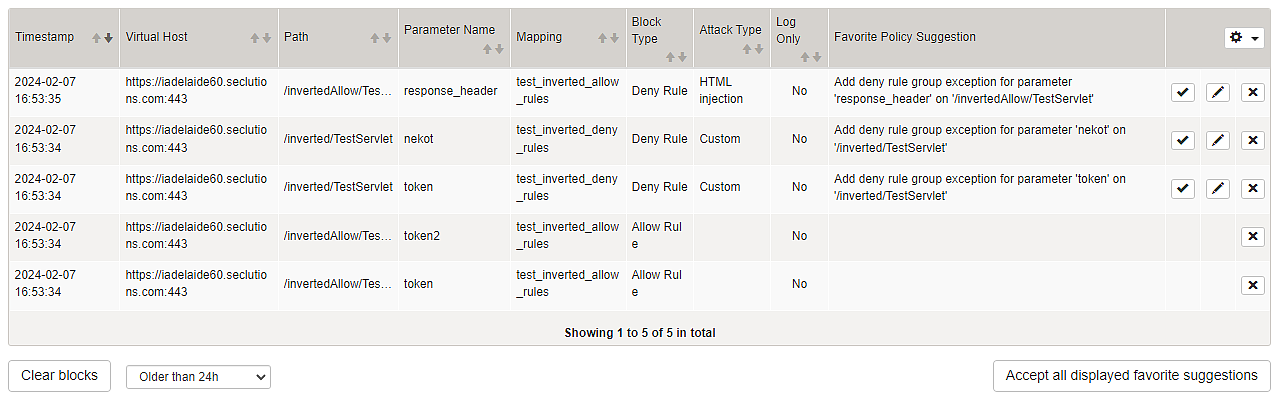
The policy learning dashboard gives an overview of requests violating the current security policy (of deny and allow rules) in place. For each violating request, the request details are stored in a database. Automatically generated suggestions for preventing similar violations are offered and can be accepted with a single click from the result table.
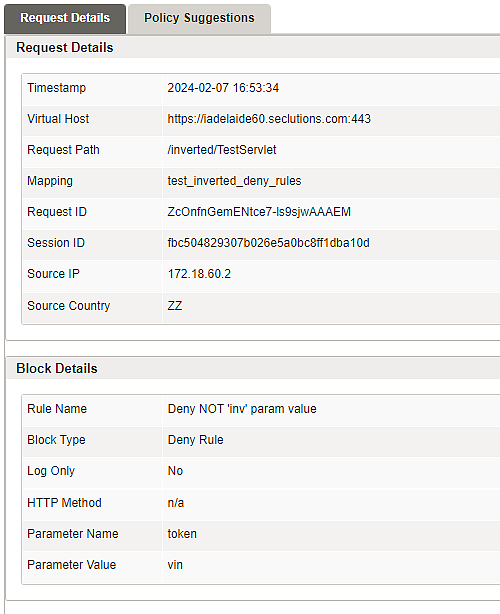
The table itself can be filtered and allows drilling down into specific requests to investigate the root cause of the violation. This enables administrators to quickly integrate new applications by remediating false-positive blocks and learning allow list rules.
- Only violations caused by Deny Rules and Allow Rules are visible in the policy learning dashboard. The set of covered violations will be continually extended.
- Parameters and header values may be trimmed before storing them in the block list.
- Use
%as a wildcard in filter criteria. - Use
ZZas a pseudo country code wildcard to filter for country-less source IP addresses. - The state of a handled block message and the configuration change related to the accepted suggestion are stored in the current administrator session. This means all decisions can be undone by re-logging into the Configuration Center.
To learn how to use policy learning, see article Using the policy learning feature.
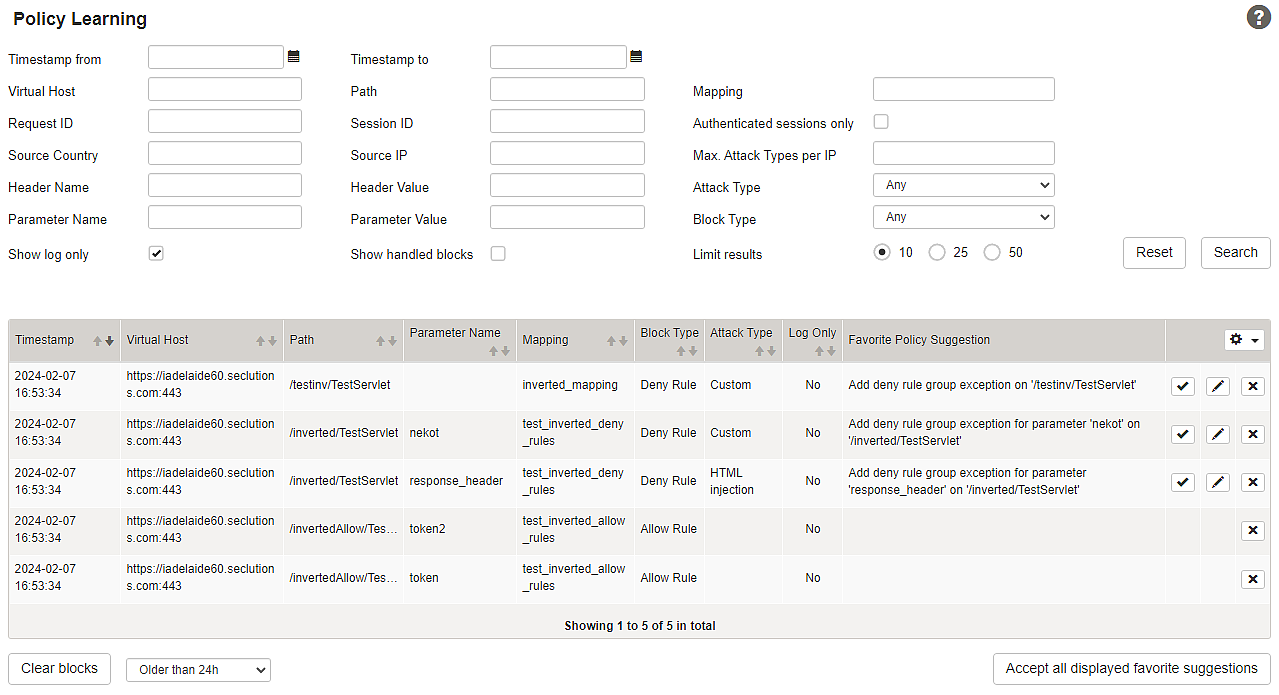
Option | Description | ||
|---|---|---|---|
Timestamp from – | To set a time window for the listed blocks. | ||
Virtual Host – | Defines the mapping-related path of the request from which blocks are to be listed.
| ||
Request ID | Filter for the ID of the request. | ||
Session ID | Filter ID of the session. | ||
Authenticated sessions only | Filter to show blocks that occurred during authenticated sessions. | ||
Source Country | Filter for a two-letter ISO country of origin of the request. This filter is not case-sensitive and allows searching for single letters. | ||
Source IP | Filter for Request IP. | ||
Max. Attack Types per IP | Filter based on the number of attacks of different types originating from the same IP source. | ||
Header Name – | Filter for HTTP header name and value of the request. | ||
Attack Type | Available attack type filters:
| ||
Parameter Name – | Filter for parameter name and value of the request. | ||
Block Type | Filter to select the applying rule type for results. Can be set to Any, Allow Rule or Deny Rule. | ||
Show log only | If threat handling on a mapping or filter is set to Log only, requests are not blocked but a notification about the potential block is written to the logs instead. | ||
Show handled blocks | Blocks already processed by accepting a generated suggestion or by ignoring the block are marked as handled. | ||
Limit results | Limits the number of listed results. |