Configuring Traffic Matchers is an optional step. The following example can be used as anomaly detection exclusion to exclude, i.e., vulnerability scans during training data collection. It can also be used in production mode as a response rule exception.
Traffic matchers are configured as sets of regex filters and IP Lists that can be applied to incoming traffic.
- Traffic Matchers are resources for the Anomaly Shield Applications detail page and can be referenced under:
- Training Data Collection, e.g., to exclude vulnerability scanning sessions from being analyzed and collected as training data by Airlock Anomaly Shield.
- Anomaly Detection Exclusions to bypass potentially non-threatening sessions (e.g., internal network traffic) around Airlock Anomaly Shield.
- Response Rule Exceptions to prevent false positives and matching requests bypass the Airlock Anomaly Shield. Other requests of the same session are not affected by the exclusion and are processed by Airlock Anomaly Shield as usual.
- To configure Traffic Matchers:
- Go to:
Application Firewall >> Anomaly Shield >> tab Traffic Matchers - Click the + button to create a new traffic matcher.
- The Anomaly Shield Traffic Matchers detail page opens up.
- Set the filter conditions in the section Matching Conditions. The following is a simple example configuration that excludes traffic from known IP addresses from being computed by Anomaly Shield. Typical usage is to exclude traffic from internal vulnerability scans:
- Apply the traffic matcher to the section Anomaly Detection on the Anomaly Shield Application detail page.
- Activate the configuration.
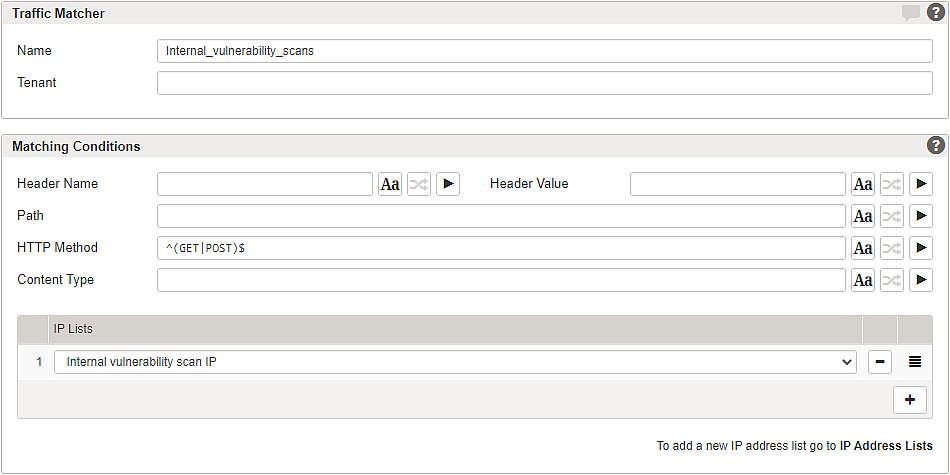
Note that our example only uses an IP filter. IP Lists are managed here: Submenu – IP Address Lists.
You can add additional traffic matchers with more complex filter conditions, for example, by specifying a path and HTTP Method to be ignored.
.theme/1.2/en-us.AAS_application_with_Traffic_Matcher_(detail_page)_html.png)