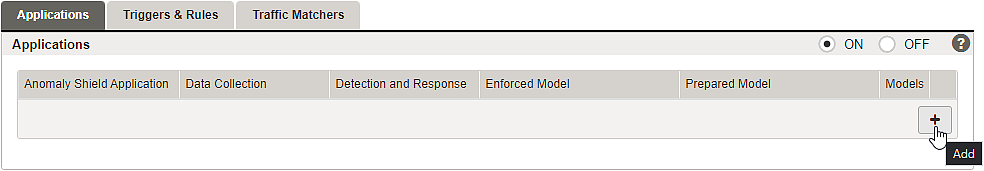
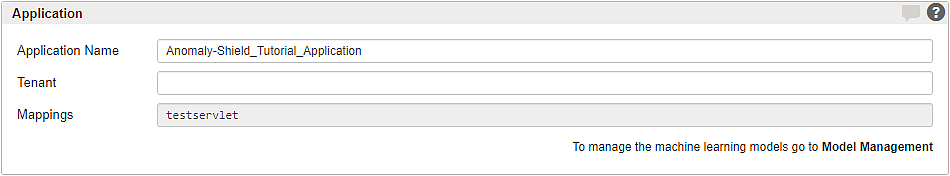
To shield back-end groups and applications with Airlock Anomaly Shield, one or more Anomaly Shield applications must be configured. Airlock Anomaly Shield's machine learning algorithms must be trained with production data to detect anomalous or suspicious traffic. Different applications do have different traffic behavior, and therefore it is important to individually configure and train multiple Anomaly Shield applications to effectively detect anomalies.
- The following guidelines may help to determine if mappings should use different Anomaly Shield applications or not:
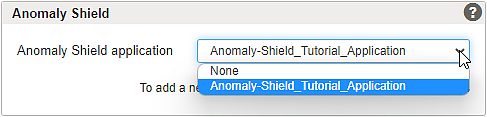
- Airlock IAM is a separate backend system that has unique characteristics in how it interacts with both REST and browser clients. Airlock IAM mappings should almost always be in a separate Anomaly Shield Application.
- If there is no good reason to assign a single Anomaly Shield application to multiple mappings, it is recommended to configure and train separate Anomaly Shield applications per mapping.
- If multiple mappings are connected to a single back-end application (e.g. Wordpress), then only one Anomaly Shield application should be assigned on all corresponding mappings.
- If a back-end or back-end group provides services to multiple different applications (e.g. separate e-banking and trading apps) through a single mapping, this mapping should be split up into one mapping per back-end application. For each mapping, a separate Anomaly Shield application should be configured and assigned.
_applications_in_Data_Collection_mode.theme/1.2/en-us.AAS_(no_dropshadow)_applications_in_Data_Collection_mode_html.png)