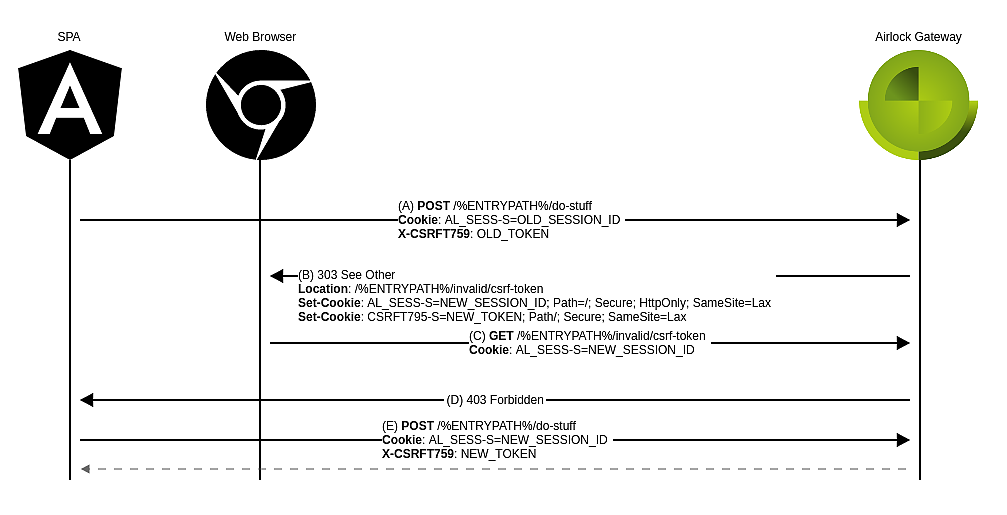
Set the invalid token redirect location in the CSRF Tokens tab on the corresponding mapping to /%ENTRYPATH%/invalid/csrf-token.
Note that the exact path is not important as long as the configured value does not collide with any URL used in your application.
To ensure that the SPA can handle the gateway's response, transform the redirect into for example a 403 Forbidden.
To do so, set the following Apache Expert Settings on the corresponding mapping:
RewriteEngine On
RewriteRule "invalid/csrf-token" "-" [F]
The path in the rewrite rule must match the previously configured invalid token redirect location. With this rewrite rule, any request to /%ENTRYPATH%/invalid/csrf-token will be responded to by a 403 Forbidden.
- The changes above ensure that in case of a CSRF block:
- The user's session ID and CSRF token will be renewed. These new values are delivered as cookies in the gateway's response (
303 See Other towards /%ENTRYPATH%/invalid/csrf-token) to the CSRF block. - The user's browser follows the redirect and effectuates a
GET /%ENTRYPATH%/invalid/csrf-token which is answered by a 403 Forbidden. This error is propagated to your SPA which can then handle it appropriately.