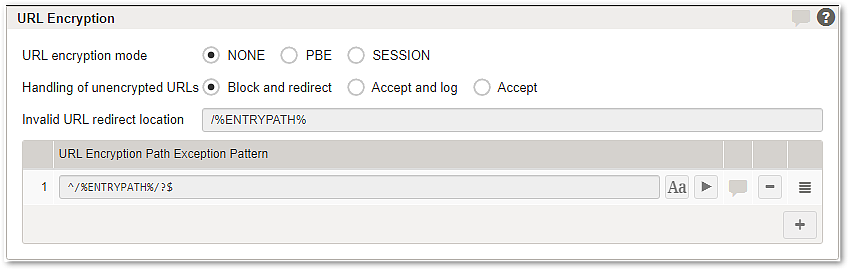
| - NONE – URL encryption mode is disabled.
- PBE – Passphrase-based encryption (PBE) is enabled.
PBE makes it possible to have encrypted URLs, parameters and values that are valid over multiple user sessions. - SESSION – Session-based encryption is enabled.
This is the recommended setting. When enabled, all cryptographically encrypted values are only valid during a user's session.
|
Handling of unencrypted URLs | - Block and redirect – Request URLs must be encrypted. This is enforced by redirecting requests that contain an unencrypted URL to the invalid URL redirect location.
- This setting protects against cross-site request forgery (CSRF) and forceful browsing (no tampering with URL and parameters possible).
- It also provides information hiding.
- This is the most secure setting.
- Accept and log – Encrypted and unencrypted request URLs are accepted. A log message is written when an unencrypted request URL is detected.
- Form protection is not possible.
- This setting provides information hiding only.
- It does not protect against cross-site request forgery (CSRF) or forceful browsing!
- Accept – Encrypted and unencrypted request URLs are accepted.
- Form protection is not possible.
- This setting provides information hiding only.
- It does not protect against cross-site request forgery (CSRF) or forceful browsing!
|
Invalid URL redirect location | - Defines the redirect location to redirect the user to if an invalid URL is detected. Invalid URLs may occur because of session timeouts or other terminated sessions and do not imply active attacks in all cases.
Example:
/index.html |
URL Encryption Path Exception Pattern | - Once the URL encryption engine is activated for a back-end mapping, Airlock Gateway only accepts encrypted URLs to access this application. However, there must be so-called bookmark or entry URLs configured that are accessible without encryption to get into the application context in the first place.
- The exception patterns can be configured in a list of regular expressions. All incoming URLs that match one of these patterns are accepted by Airlock Gateway without encryption. The ignore case (ICase) option specifies whether the pattern should be interpreted case insensitive.
Note:
The Invalid URL redirect location must be one of these exceptions if it is located behind the same URL mapping. Otherwise, a continuous redirect loop is initiated. It is recommended to only allow very simple and static URLs to be accessed as exceptions. The following example specifies that the basic URL /index.html may be accessed without encryption. This way, users can bookmark the index page in their browsers. From that point, all URLs are encrypted. - Example:
^/index\.html$ ^/%ENTRYPATH%/?$
|