To assist the administrator in accepting the appropriate suggestion, the number of blocks covered is indicated in the 'Blocks Covered' column. For instance, if a very generic suggestion covers only few blocks, more specific suggestion should be accepted instead. However, if a generic suggestion covers many blocks that would otherwise require a lot of specific suggestions, it may be better accepting the generic suggestion.
For each block, the favorite suggestion is presented in the result table as a shortcut and can be accepted by clicking the 'Accept' icon on the right side.
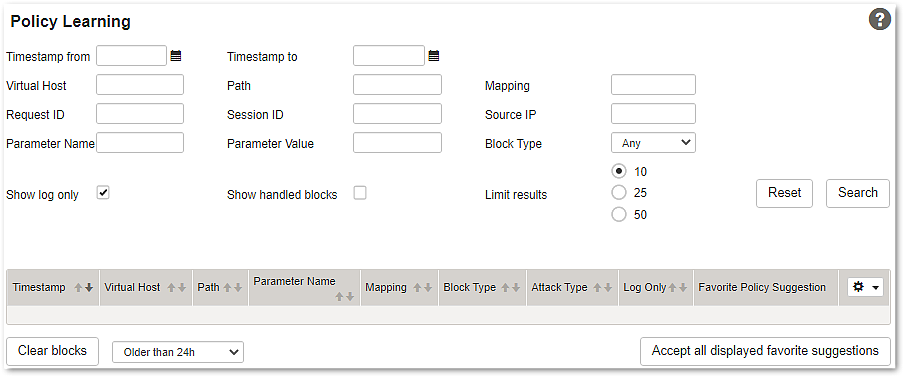
On top of the 'Accept' icon column, an 'Accept all' icon is located. By clicking 'Accept all', all currently displayed favorite suggestions are automatically accepted. The currently displayed favorite suggestions are those visible in the result table as defined by the filter criteria and the chosen result size (10, 25, or 50).
Accepting all favorite suggestions at once is a powerful option when filtered blocks originate form traffic that is generally trusted, e.g., because it originates from a set of internal test clients. However, we do not recommend using this feature without carefully reviewing all suggestions.
For accepting alternative suggestions, open the tab 'Policy Suggestions' and accept any of the listed suggestions.